Access-list Questions
If you are not sure about Access-list, please read our Access-list tutorial.
Question 1
Explanation
Remember, for the wildcard mask, 1′s are I DON’T CARE, and 0′s are I CARE. So now let’s analyze a simple ACL:
access-list 1 permit 172.23.16.0 0.0.15.255
Two first octets are all 0’s meaning that we care about the network 172.23.x.x. The third octet of the wildcard mask, 15 (0000 1111 in binary), means that we care about first 4 bits but don’t care about last 4 bits so we allow the third octet in the form of 0001xxxx (minimum:00010000 = 16; maximum: 0001111 = 31).
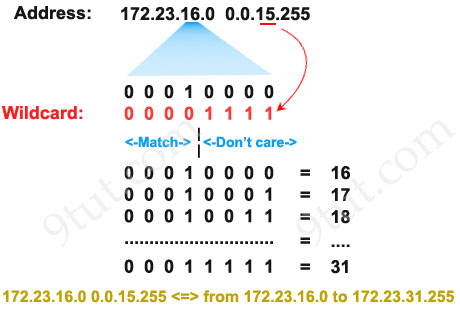
The fourth octet is 255 (all 1 bits) that means I don’t care.
Therefore network 172.23.16.0 0.0.15.255 ranges from 172.23.16.0 to 172.23.31.255.
Now let’s consider the wildcard mask of 0.0.0.254 (four octet: 254 = 1111 1110) which means we only care the last bit. Therefore if the last bit of the IP address is a “1” (0000 0001) then only odd numbers are allowed. If the last bit of the IP address is a “0” (0000 0000) then only even numbers are allowed.
Note: In binary, odd numbers are always end with a “1” while even numbers are always end with a “0”.
Therefore in this question, only the statement “permit 10.0.0.1 0.0.0.254” will allow all odd-numbered hosts in the 10.0.0.0/24 subnet.
Question 2
Question 3
Explanation
The syntax of an extended ACL is shown below:
access-list access-list-number {permit | deny} protocol source {source-mask} [eq source-port] destination {destination-mask} [eq destination-port]
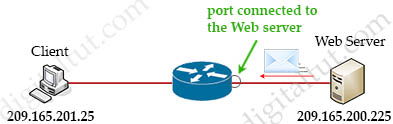
According to the request in this question, we must apply the ACL on the port connected to the Web Server and with inbound direction. So it can only filter traffic sent from the Web Server to the Client. Please notice that the Client communicate to the Web Server with destination port of 80 but with random source port. So the Web Server must answer the Client with this random port (as the destination port) -> Therefore the destination port in the required ACL must be ignored. Also the Web Server must use port 80 as its source port.
So the structure of the ACL should be: permit tcp host <IP-address-of-Web-Server> eq 80 host <IP-address-of-Client>
-> Answer C is correct.
Question 4
Explanation
Although the statement “permit tcp any any gt … lt …” seems to be correct but in fact it is not. Each ACL statement only supports either “gt” or “lt” but not both:
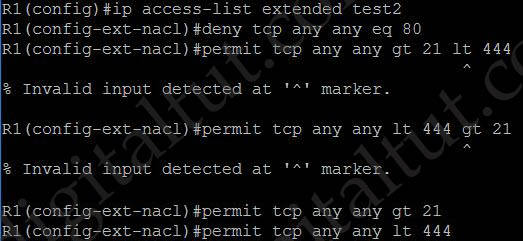
-> Answer A is not correct.
Answer C is only correct if the order of the statement is in reverse order.
Question 5
Explanation
We can insert a line (statement) between entries into an existing ACL by a number in between.
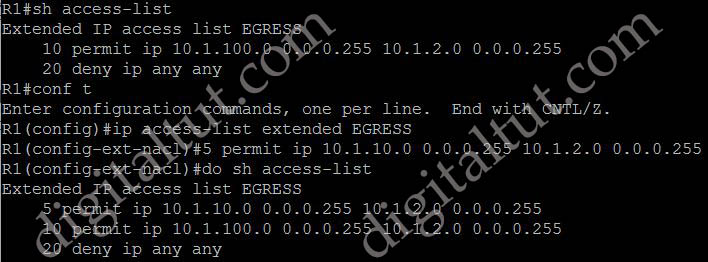
So what will happen if we just enter a statement without the number? Well, that statement would be added at the bottom of an ACL. But in this case we already had an explicit “deny ip any any” statement so we cannot put another line under it.
Question 6
Explanation
We cannot filter traffic that is originated from the local router (R3 in this case) so we can only configure the ACL on R1 or R2. “Weekend hours” means from Saturday morning through Sunday night so we have to configure: “periodic weekend 00:00 to 23:59”.
Note: The time is specified in 24-hour time (hh:mm), where the hours range from 0 to 23 and the minutes range from 0 to 59.
Question 7
Explanation
The established keyword is only applicable to TCP access list entries to match TCP segments that have the ACK and/or RST control bit set (regardless of the source and destination ports), which assumes that a TCP connection has already been established in one direction only. Let’s see an example below:
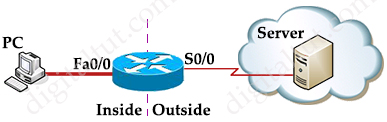 Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
Suppose you only want to allow the hosts inside your company to telnet to an outside server but not vice versa, you can simply use an “established” access-list like this:
| access-list 100 permit tcp any any established access-list 101 permit tcp any any eq telnet ! interface S0/0 ip access-group 100 in ip access-group 101 out |
Note:
Suppose host A wants to start communicating with host B using TCP. Before they can send real data, a three-way handshake must be established first. Let’s see how this process takes place:
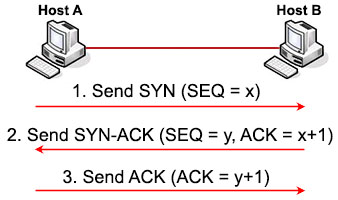
1. First host A will send a SYN message (a TCP segment with SYN flag set to 1, SYN is short for SYNchronize) to indicate it wants to setup a connection with host B. This message includes a sequence (SEQ) number for tracking purpose. This sequence number can be any 32-bit number (range from 0 to 232) so we use “x” to represent it.
2. After receiving SYN message from host A, host B replies with SYN-ACK message (some books may call it “SYN/ACK” or “SYN, ACK” message. ACK is short for ACKnowledge). This message includes a SYN sequence number and an ACK number:
+ SYN sequence number (let’s called it “y”) is a random number and does not have any relationship with Host A’s SYN SEQ number.
+ ACK number is the next number of Host A’s SYN sequence number it received, so we represent it with “x+1”. It means “I received your part. Now send me the next part (x + 1)”.
The SYN-ACK message indicates host B accepts to talk to host A (via ACK part). And ask if host A still wants to talk to it as well (via SYN part).
3. After Host A received the SYN-ACK message from host B, it sends an ACK message with ACK number “y+1” to host B. This confirms host A still wants to talk to host B.
Question 8
Explanation
The inbound direction of G0/0 of SW2 only filter traffic from Web Server to PC-1 so the source IP address and port is of the Web Server.
Question 9
Explanation
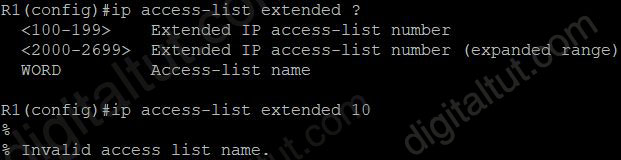
Note: We cannot assign a number smaller than 100 to an extended access-list so the command “ip access-list extended 10” is not correct.
Question 10
Explanation
We see in the traceroute result the packet could reach 10.99.69.5 (on R2) but it could not go any further so we can deduce an ACL on R3 was blocking it.
Note: Record option displays the address(es) of the hops (up to nine) the packet goes through.



Where can I get the questions for these answers?
shouldn’t question 4’s answer be D ?
Why B, not D
Question 3
A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web server. Which statement allows this traffic?
A. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
B. permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
C. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
D. permit tcp host 209.165.200.225 host 209.165.201.25 eq 80
Answer: B
Question 3
“in the inbound direction on the port connecting to the web server”
this direction from “port where connect web-server” point of view is from webserver 209.165.200.225 port 80 to client 209.165.201.25
answer should be A.
@digitut. The question 3 is wrong. is the duplicated one. A or C. thxs
Q3 is either A or C because the questions states the ACL is applied in inbound direction in the port CONNECTED TO THE SERVER.
@whoamI, @Chromatica II: Thanks for your detection, we have just updated Q.3
@digitaltut can you update this also on the access-list-questions quiz? its not updated on the quiz. thanks
@digitaltut – answer on the site and on the quiz (answer is letter B on the quiz) is different please update it. thanks a lot!
Question 3
A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web server. Which statement allows this traffic?
A. permit tcp host 209.165.201.25 eq 80 host 209.165.200.225
B. permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
C. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
D. permit tcp host 209.165.200.225 host 209.165.201.25 eq 80
Answer: C
A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web server. Which statement allows this traffic?
A. permit tcp host 209.165.201.25 eq 80 host 209.165.200.225
B. permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
C. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
D. permit tcp host 209.165.200.225 host 209.165.201.25 eq 80
Ans should be B … Because in inbound direction towards server , source IP would be client IP not server IP .. When server replies i.e outbound direction , source IP would be server.
So , inbound traffic to server would be as follows :
Source IP : 209.165.201.25 , Destination IP:Port : 209.165.200.225:80
Question 4
Which access controls list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
A. Deny tcp any any eq 80
Permit tcp any any gt 21 lt 444
B. Permit tcp any any neq 80
C. Permit tcp any any range 22 443
Deny tcp any any eq 80
D. Deny tcp any any neq 80
Permit tcp any any range 22 443
Answer should be B
Question 3 is B
Question 2
Refer to the exhibit. An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthemet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet. Which explanation of this behavior is true?
Extended IP access list EGRESS
10 permit ip 10.0.0.0 0.0.0.255 any
!
—output omitted—
!
interface GigabitEthernet0/0
ip address 209.165.200.255/24 <– Broadcast ??
ip access-group EGRESS out
duplex auto
speed auto
media-type rj45
!
Question 4
Which access controls list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
A. Deny tcp any any eq 80
Permit tcp any any gt 21 lt 444
B. Permit tcp any any neq 80
C. Permit tcp any any range 22 443
Deny tcp any any eq 80
D. Deny tcp any any neq 80
Permit tcp any any range 22 443
the first command should be *Deny tcp any any eq 80* this command cant be in 2nd line
I THINK D will be correct
Sorry i missed “neq” D is also wrong of it was “eq 80” then D would be correct
Question 4
Which access controls list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
A. Deny tcp any any eq 80
Permit tcp any any gt 21 lt 444
B. Permit tcp any any neq 80
C. Permit tcp any any range 22 443
Deny tcp any any eq 80
D. Deny tcp any any neq 80
Permit tcp any any range 22 443
B is correct. The question indicates ONLY TCP, then it’s reffered to protocol only, and not to port range. Therefore B exclude port 80 and permit all port, only TCP
Question 4
Which access controls list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
A. Deny tcp any any eq 80 Permit tcp any any gt 21 lt 444
B. Permit tcp any any neq 80
C. Permit tcp any any range 22 443 Deny tcp any any eq 80
D. Deny tcp any any neq 80 Permit tcp any any range 22 443
answer A 100%
@digitaltut Q4: We are saying option it the best choiced. But on the premium member test link that same answer is marked as wrong not sure if it is an error.
Option A
@Paswd: Thanks for your detection, we have just updated Q.4.
Q3 based on explanation under the question answer should be D
The syntax of an extended ACL is shown below:
access-list access-list-number {permit | deny} protocol source {source-mask} destination {destination-mask} [eq destination-port]
Please correct me if I am wrong
@hello: That explanation was missing [eq source-port] part. Thanks for your detection, we have just updated it but the answer is still correct.
Answer should be
Deny tcp any any eq 80
Permit tcp any any range 22 443
So there is a typo somewhere!
Agree with Kuku. question 4 in the set of questions above does not have a correct answer. Close enough is not possible when the syntax does not allow a particular format.
The Deny and Permit supplied by Kuku above is a correct and efficient solution.
Agree to @Mark, Q4, best answer should be B.
permit tcp any any neq 80, which will permit all other tcp ports except tcp/80. Fulfilled the question.
A. Deny tcp any any eq 80
Permit tcp any any gt 21 lt 444
(command syntax is not valid)
C. Permit tcp any any range 22 443
Deny tcp any any eq 80
(correct syntax, but wrong order)
D. Deny tcp any any neq 80
Permit tcp any any range 22 443
(correct syntax, but that’s not what Q is asking for.)
@contoso RE Q4:
The problem statement has 2 requirements:
1- Which access controls list allows only TCP traffic with a destination port range of 22-443
2- Excluding port 80
simply: permit tcp any any neq 80 meets the second, but NOT the first requirement.
As written, there is NOT a correct solution. Close enough when the syntax is not supported is NOT close enough.
As I stated earlier, there must be a typo in there as none of the answers is valid.
Graphic is wrong. Look at the “permits from odd-numbered hosts” question.
It *should* look like this:
00010000=16
00010001=17
00010010=18
00010011=19
It shows the wrong bits on for the decimal value of 18.
4 should be B
B does exclude port 80 from the allowed range of ports “permit tcp any any neq 80 ”
-permit everything that is not equal to 80-
A is wrong because you cannot have “Each ACL statement only supports either “gt” or “lt” but not both”
C is wrong because of the order of the ACEs
D is wrong because “Deny tcp any any neq 80” will deny tcp any that is non equal to 80.
-Permitting everything with port 80-
Question 3
the answer should be B. TCP traffic from the client (209.165.201.25) to the web server (209.165.200.225) on destination port 80
Question 3
client (209.165.201.25) will use random port on connecting to web server (209.165.200.225) port 80.
Question 3
My bad, it is inbound direction in wan interface. Hehe
Question 3
the answer should be B. source of the IP is 209.165.201.25 and destination is web 209.165.200.225 on destination port 80.
No matter the direction of the traffic is, inbound or outbound, the source should still be at the beginning.
permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
sorry got confused there. please ignore.
I agree with nickname, answer should be B, @digitaltut could you confirm please?
Question 1
Which standard access control entry permits from odd-numbered hosts in the 10.0.0.0/24 subnet?
A. Permit 10.0.0.0 0.0.0.1
B. Permit 10.0.0.1 0.0.0.0
C. Permit 10.0.0.1 0.0.0.254
D. Permit 10.0.0.0 255.255.255.254
A. Permit 10.0.0.0 0.0.0.1 – This would permit access only from the first address (10.0.0.0) and the second address (10.0.0.1), not just odd-numbered hosts.
B. Permit 10.0.0.1 0.0.0.0 – This would permit access only from the address 10.0.0.1, not from odd-numbered hosts.
C. Permit 10.0.0.1 0.0.0.254 – This option is incorrect because it would allow access from both even and odd-numbered hosts.
D. Permit 10.0.0.0 255.255.255.254 – This option would permit access from all hosts in the subnet except for the last one (10.0.0.254), meaning it includes both even and odd-numbered hosts.
Among the given options, none of them directly permit access only from odd-numbered hosts in the 10.0.0.0/24 subnet. However, if we were to choose the closest option, it would be option C. Permit 10.0.0.1 0.0.0.254, which permits access from hosts with odd-numbered last octets but also includes even-numbered hosts. Therefore, none of the options are entirely correct for permitting access only from odd-numbered hosts.
Also Option c has the wrong wild card mask set, it should be 0.0.0.255 for a /24 network
@The great Gateway: Option C has correct wild card mask of 0.0.0.254 (not 255) to allow odd-numbered hosts. If the wild card mask is 255 then all the hosts (10.0.0.x) are allowed.
Question 1
C. Permit 10.0.0.1 0.0.0.254
What is the subnet mask for the wildcard 0.0.0.254? I don’t quite understand it properly. Thanks.