Automation Questions
Note: If you are not sure about Automation, please read our JSON Tutorial, JSON Web Token (JWT) Tutorial, Ansible Tutorial, Chef Tutorial, Puppet Tutorial.
|
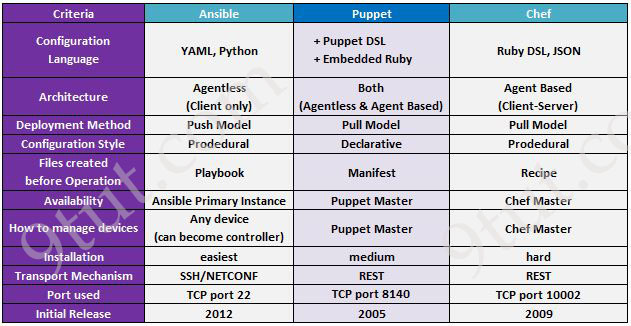
Quick summary about Ansible, Puppet, Chef
JSON Quick summary JavaScript Object Notation (JSON) is a human readable and very popular format used by web services, programming languages (including Python) and APIs to read/write data. JSON syntax structure: JSON can use arrays. Arrays are used to store multiple values in a single variable. For example: {
“name”:”John”,
“age”:30,
“cars”:[ “Ford”, “BMW”, “Fiat”]
}
In the above example, “cars” is an array which contains three values “Ford”, “BMW” and “Fiat”. If we have a JSON string, we can convert (parse) it into Python by using the import json
myvar = '{“name”:”John”,“age”:30,“cars”:[ “Ford”, “BMW”, “Fiat”]}'
parse_myvar = json.loads(myvar)
print(parse_myvar["cars"][0])
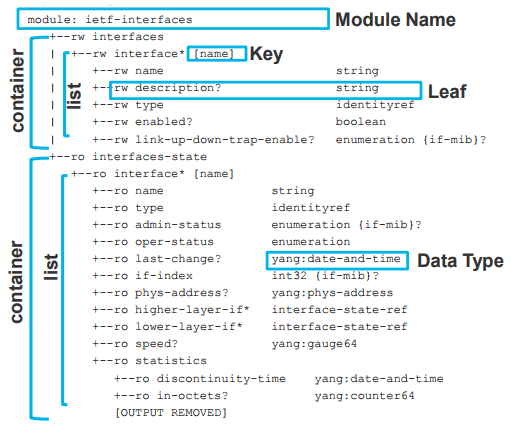
The result: Ford Note: NETCONF Quick summary NETCONF provides mechanisms to retrieve and manipulate configuration of network devices. NETCONF is very similar to Command Line Interface (CLI) we all knew. But the main difference is CLI is designed for humans while NETCONF is aimed for automation applications. NETCONF protocol is based on XML messages exchanged via SSH protocol using TCP port 830 (default). Network devices running a NETCONF agent can be managed through five main operations: The NETCONF protocol requires messages to always be encoded with XML. RESTCONF Quick summary RESTCONF helps NETCONF to run on the most popular protocol on the Internet: HTTP/HTTPS. Network devices running a RESTCONF agent can be managed through five HTTP operations: The RESTCONF protocol allows data to be encoded with either XML or JSON. YANG Quick summary YANG (Yet Another Next Generation) is a data modelling language, providing a standardized way to model the operational and configuration data of a network device. YANG can then be converted into any encoding format, e.g. XML or JSON. An example of a YANG model is shown below (source: Cisco Live DEVNET-1721):
|
Question 1
Explanation
Ansible-managed node can be a Juniper device or other vendors’ device as well so answer A is not correct.
Ansible communicates with managed node via SSH -> Answer B is correct.
An Ansible ad-hoc command uses the /usr/bin/ansible command-line tool to automate a single task on one or more managed nodes. Ad-hoc commands are quick and easy, but they are not reusable -> It is not a requirement either -> Answer C is not correct.
Ansible Tower is a web-based solution that makes Ansible even more easy to use for IT teams of all kinds. But it is not a requirement to run Ansible -> Answer D is not correct.
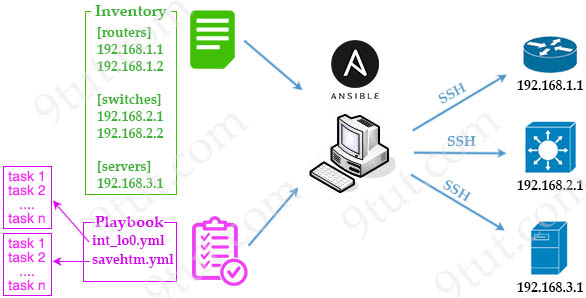
Note: Managed Nodes are the network devices (and/or servers) you manage with Ansible. Managed nodes are also sometimes called “hosts”. Ansible is not installed on managed nodes.
Question 2
Explanation
When a device boots up with the startup configuration, the nginx process will be running. NGINX is an internal webserver that acts as a proxy webserver. It provides Transport Layer Security (TLS)-based HTTPS. RESTCONF request sent via HTTPS is first received by the NGINX proxy web server, and the request is transferred to the confd web server for further syntax/semantics check.
The https-based protocol-RESTCONF (RFC 8040), which is a stateless protocol, uses secure HTTP methods to provide CREATE, READ, UPDATE and DELETE (CRUD) operations on a conceptual datastore containing YANG-defined data -> RESTCONF only uses HTTPs.
Note: In fact answer C is also correct:
RESTCONF servers MUST present an X.509v3-based certificate when establishing a TLS connection with a RESTCONF client. The use of X.509v3-based certificates is consistent with NETCONF over TLS.
Reference: https://tools.ietf.org/html/rfc8040
But answer A is still a better choice.
Question 3
Explanation
RESTCONF operations include OPTIONS, HEAD, GET, POST, PUT, PATCH, DELETE.
| RESTCONF | Description |
| OPTIONS | Determine which methods are supported by the server. |
| GET | Retrieve data and metadata about a resource. |
| HEAD | The same as GET, but only the response headers are returned. |
| POST | Create a resource or invoke an RPC operation. |
| PUT | Create or replace a resource. |
| PATCH | Create or update (but not delete) various resources. |
| DELETE | Sent by a client to delete a target resource. |
Question 4
Question 5
Explanation
An EEM policy is an entity that defines an event and the actions to be taken when that event occurs. There are two types of EEM policies: an applet or a script. An applet is a simple form of policy that is defined within the CLI configuration. A script is a form of policy that is written in Tool Command Language (Tcl).
There are two ways to manually run an EEM policy. EEM usually schedules and runs policies on the basis of an event specification that is contained within the policy itself. The event none command allows EEM to identify an EEM policy that can be manually triggered. To run the policy, use either the action policy command in applet configuration mode or the event manager run command in privileged EXEC mode.
Question 6
Explanation
EEM offers the ability to monitor events and take informational or corrective action when the monitored events occur or reach a threshold. An EEM policy is an entity that defines an event and the actions to be taken when that event occurs. There are two types of EEM policies: an applet or a script. An applet is a simple form of policy that is defined within the CLI configuration.
To specify the event criteria for an Embedded Event Manager (EEM) applet that is run by sampling Simple Network Management Protocol (SNMP) object identifier values, use the event snmp command in applet configuration mode.
event snmp oid oid-value get-type {exact | next} entry-op operator entry-val entry-value [exit-comb {or | and}] [exit-op operator] [exit-val exit-value] [exit-time exit-time-value] poll-interval poll-int-value
+ oid: Specifies the SNMP object identifier (object ID)
+ get-type: Specifies the type of SNMP get operation to be applied to the object ID specified by the oid-value argument.
— next – Retrieves the object ID that is the alphanumeric successor to the object ID specified by the oid-value argument.
+ entry-op: Compares the contents of the current object ID with the entry value using the specified operator. If there is a match, an event is triggered and event monitoring is disabled until the exit criteria are met.
+ entry-val: Specifies the value with which the contents of the current object ID are compared to decide if an SNMP event should be raised.
+ exit-op: Compares the contents of the current object ID with the exit value using the specified operator. If there is a match, an event is triggered and event monitoring is reenabled.
+ poll-interval: Specifies the time interval between consecutive polls (in seconds)
Reference: https://www.cisco.com/en/US/docs/ios/12_3t/12_3t4/feature/guide/gtioseem.html
In particular, this EEM will read the next value of above OID every 5 second and will trigger an action if the value is greater or equal (ge) 75%.
Question 7
Explanation
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
JSON Web Tokens are composed of three parts, separated by a dot (.): Header, Payload, Signature. Therefore, a JWT typically looks like the following:
xxxxx.yyyyy.zzzzz
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA.
The second part of the token is the payload, which contains the claims. Claims are statements about an entity (typically, the user) and additional data.
To create the signature part you have to take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
Reference: https://jwt.io/introduction/
Question 8
Explanation
When you use the sync yes option in the event cli command, the EEM applet runs before the CLI command is executed. The EEM applet should set the _exit_status variable to indicate whether the CLI command should be executed (_exit_status set to one) or not (_exit_status set to zero).
With the sync no option, the EEM applet is executed in background in parallel with the CLI command.
Reference: https://blog.ipspace.net/2011/01/eem-event-cli-command-options-and.html
Question 9
Question 10
Explanation
YANG (Yet Another Next Generation) is a data modeling language for the definition of data sent over network management protocols such as the NETCONF and RESTCONF.
Question 11
Explanation
The REST API accepts and returns HTTP (not enabled by default) or HTTPS messages that contain JavaScript Object Notation (JSON) or Extensible Markup Language (XML) documents. You can use any programming language to generate the messages and the JSON or XML documents that contain the API methods or Managed Object (MO) descriptions.
Question 12
Explanation
This JSON can be written as follows:
{
"switch": {
"name": "dist1",
"interfaces": ["gig1", "gig2", "gig3"]
}
}



Question 3
Which two operations are valid for RESTCONF? (Choose two)
A. HEAD
B. REMOVE
C. PULL
D. PATCH
E. ADD
F. PUSH
should A and D with the given explanation: RESTCONF operations include OPTIONS, HEAD, GET, POST, PATCH, DELETE.
Question 5
Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
A. event manager applet ondemand
event register
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
B. event manager applet ondemand
event manual
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
C. event manager applet ondemand
event none
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
D. event manager applet ondemand
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
Answer: A
Should be C – The event none command allows EEM to identify an EEM policy that can be manually triggered. To run the policy, use either the action policy command in applet configuration mode or the event manager run command in privileged EXEC mode.
@Ciscolad: Yes, thanks for your detection, we have just fixed them!
@ Ciscolad
I agree with you for Q3, correct answer A and D
No worries guys, glad to help and contribute :)
Q2.
NGINX is an internal webserver that acts as a proxy webserver. It provides Transport Layer Security (TLS)-based HTTPS. RESTCONF request sent via HTTPS is first received by the NGINX proxy web serve,r and the request is transferred to the confd web server for further syntax/semantics check.
Source:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/prog/configuration/171/b_171_programmability_cg/restconf_protocol.html
Question 6 :
What does this EEM applet event accomplish?
“event snmp oid 1.3.6.1.3.7.1.5.1.2.4.2.9 get-type next entry-op go entry-val 75 poll-interval 5”
A. It issues email when the value is greater than 75% for five polling cydes
B. It reads an SNMP variable, and when the value exceeds 75%, it triggers an action GO
C. It presents a SNMP variable that can be interrogated
D. Upon the value reaching 75%, a SNMP event is generated and sent to the trap server
how come to have go as a word here, i think should be here operator not a go maybe ge.
could you please review the question
@Anonymous: Thanks for your detection, it should be “ge” not “go”. We updated Q.6.
son todas las preguntas?
Which requirement for an Ansible-managed node is true?
A. It must be a Linux server or a Cisco device
B. It must have an SSH server running
C. It must support ad hoc commands.
D. It must have an Ansible Tower installed
Answer I believe is B. While it is true Ansible cannot be installed on Windows machine, it cannot also be installed on Cisco cisco device so A is wrong. However for All Ansible managed host i.e cisco device, windows device, etc, SSH must be running to manage them. This is one of those sneaky ones by Cisco I believe
Chuck Norris,
I think so.
Cert guide says:
Ansible is an agentless tool. …
Ansible communicates using SSH for a majority of devices, and it can support Windows Remote Management (WinRM) and other transport methods to the clients it manages. In addition, Ansible doesn’t need an administrative account on the client.
B looks correct to me as well.
Can someone please answer if CCNP 350-401 ENCOR exam has any labs? Are all questions MCQ or Drag and drops? Thanks.
@Tchow: 350-401 has no labs, it only contains MCQs and DnDs
@Chuck Noris @no-name
It looks like SSH is not the only option.
“If we want to use Ansible with them our three options are SSH, SNMP and https, where https often only gives us the same options as SSH.”
Refernce: https://packetpushers.net/ansible-cisco-snmp/#:~:text=If%20we%20want%20to%20use,the%20same%20options%20as%20SSH.
Which requirement for an Ansible-managed node is true?
A. It must be a Linux server or a Cisco device
B. It must have an SSH server running
C. It must support ad hoc commands.
D. It must have an Ansible Tower installed
Answer I believe is B. While it is true Ansible cannot be installed on Windows machine, it cannot also be installed on Cisco cisco device so A is wrong. However for All Ansible managed host i.e cisco device, windows device, etc, SSH must be running to manage them. This is one of those sneaky ones by Cisco I believe
For me its B.
Question 1
Which requirement for an Ansible-managed node is true?
B. It must have an SSH server running
https://www.tecmint.com/configure-ansible-managed-nodes-and-run-ad-hoc-commands/
As a recap on our last topic, managing remote hosts with Ansible requires setting up of Passwordless SSH authentication between the Ansible control node and the managed hosts. This involves the generation of a key pair (Public and Private SSH key pair) on the Ansible Control node and copying the Public key to all of the remote hosts. This will be a crucial step going forward and will make your work much easier.
@digitaltut it looks like Q1 answer is B. Any view on this?
@All: The correct answer for Q.1 should be B. Thanks for your detection, we updated it!
Question 8 says A and D, but that is wrong. It should be A and C.
action 1.2 gets response
action 1.3 string toupper “$response”
action 1.4 string match “$_string_result” “Y”
action 2.0 if $_string_result eq 1
The sequence:
Get keyboard input into the variable ‘response’
Convert the contents of ‘response’ into upper case and store the result in the variable ‘$_string_result’ The output of the ‘toupper’ function is stored in $_string_result
(At this point, it doesn’t matter if it was entered as upper case Y or lower case y, in $_string_result it is upper case Y.
The string match statement looks for upper case Y within ‘$_string_result’ (it will NEVER be lower case y because it was converted to upper case). If it matches $_string_result will be 1 if not it will be 0
Therefore the applet requires a case-insensitive response.
A. The EEM applet runs before the CLI command is executed
B. The EEM applet runs after the CLI command is executed
C. The EEM applet requires a case-insensitive response
D. The running configuration is displayed only if the letter Y is entered at the CLI
A is correct, but the other correct answer is C not D.
D cannot be correct because the running config is displayed if EITHER Y or y is entered.
Forgot to add link to my response to Q: 8
The Cisco IOS Embedded Event Manager Command Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/eem/command/eem-cr-book/eem-cr-a2.html
Does not look like my long response to Q:8 was accepted.
The answers are A and C; not A and D.
The toupper function makes it so that
EITHER Y or y can be used not “only Y” as specified in D
A. The EEM applet runs before the CLI command is executed
B. The EEM applet runs after the CLI command is executed
C. The EEM applet requires a case-insensitive response
D. The running configuration is displayed only if the letter Y is entered at the CLI
@Zaphod
Thanks man! Good catch!
(another pass through the list). This time on Q8, I see another problem.
Since sync=yes, then the cli cannot execute until after the EEM applet has completed.
With sync=yes is the requirement that _exit_status be set to 1 or the CLI commands will NOT run.
I do not see _exit_status being dealt with anywhere within that script.
@Digitaltut
Ans :C is correct ?
Question 10
Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools require no messaging systems between master and slaves. B. Agentless tools use proxy nodes to interface with slave nodes. C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes. D. Agent-based tools do not require installation of additional software packages on the slave nodes.
@zaphod Q8
from:https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/eem/command/eem-cr-book.pdf
“Failure to set the exit_status to 1 will cause the default action which is to skip executing the CLI
command. This can lead to situations where the router has to be reloaded in order to continue
operations.”
So D is correct too…
Hi ,
can someone from premium members send me the Automation Questions (only the first group )?
If possible I will send my email.
Thanks
@Digitaltu could you please verify Question 10 — Is Correct Ansswer C ?
Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools require no messaging systems between master and slaves.
B. Agentless tools use proxy nodes to interface with slave nodes.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require installation of additional software packages on the slave nodes.
Hello!
Does anyone have ENCOR dumps?