Miscellaneous Questions
Question 1
Explanation
Although some Cisco webpages (like this one) mentioned about “logging synchronous” command in global configuration mode, which means “Router(config)#logging synchronous”, but in fact we cannot use it under global configuration mode. We can only use this command in line mode. Therefore answer C is better than answer A.
Let’s see how the “logging synchronous” command affect the typing command:
Without this command, a message may pop up and you may not know what you typed if that message is too long. When trying to erase (backspace) your command, you realize you are erasing the message instead.
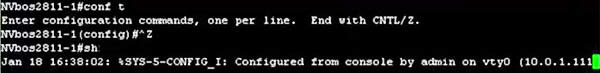
With this command enabled, when a message pops up you will be put to a new line with your typing command which is very nice:
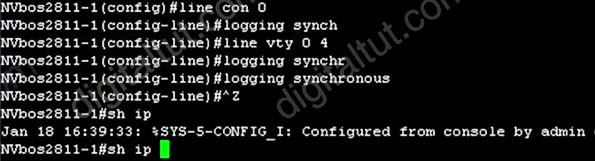
Question 2
Explanation
The Link Management Protocol (LMP) performs the following functions:
+ Verifies link integrity by establishing bidirectional traffic forwarding, and rejects any unidirectional links
+ Exchanges periodic hellos to monitor and maintain the health of the links
+ Negotiates the version of StackWise Virtual header between the switches StackWise Virtual link role resolution
Question 3
Explanation
Syslog levels are listed below:
| Level | Keyword | Description |
| 0 | emergencies | System is unusable |
| 1 | alerts | Immediate action is needed |
| 2 | critical | Critical conditions exist |
| 3 | errors | Error conditions exist |
| 4 | warnings | Warning conditions exist |
| 5 | notification | Normal, but significant, conditions exist |
| 6 | informational | Informational messages |
| 7 | debugging | Debugging messages |
Number “3” in “%LINK-3-UPDOWN” is the severity level of this message so in this case it is “errors”.
Question 4
Explanation
The application residing on Device 1 originates an RSVP message called Path, which is sent to the same destination IP address as the data flow for which a reservation is requested (that is, 10.60.60.60) and is sent with the “router alert” option turned on in the IP header. The Path message contains, among other things, the following objects:
…
–The “sender T-Spec” (traffic specification) object, which characterizes the data flow for which a reservation will be requested. The T-Spec basically defines the maximum IP bandwidth required for a call flow using a specific codec. The T-Spec is typically defined using values for the data flow’s average bit rate, peak rate, and burst size.
Reference: https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/cucm/srnd/9x/uc9x/cac.html
Question 5
Explanation
Cisco IOS Nonstop Forwarding(NSF) always runs with stateful switchover (SSO) and provides redundancy for Layer 3 traffic.



Question 7
A network administrator is implementing a routing configuration change and enables routing debugs to track routing behavior during the change. The logging output on the terminal is interrupting the command typing process. Which two actions can the network administrator take to minimize the possibility of typing commands incorrectly? (Choose two)
A. Configure the logging synchronous global configuration command
B. Configure the logging delimiter feature
C. Configure the logging synchronous command under the vty
D. Press the TAB key to reprint the command in a new line
E. Increase the number of lines on the screen using the terminal length command
A is one of the answer but cannot figure out what the other one is? either C or D seems these can be correct.
C – Use the line vty line-number command to specify which vty lines are to have synchronous logging enabled
D – If you cannot remember a complete command name, or if you want to reduce the amount of typing you have to perform, enter the first few letters of the command, then press the Tab key. The command line parser will complete the command if the string entered is unique to the command mode. If your keyboard does not have a Tab key, press Ctrl-I instead.
Anyone can shine a light on this matter?
Which two GRE features are configured to prevent fragmentation? (Choose two)
A. TCP window size
B. TCP MSS
C. IP MTU
D. DF bit Clear
E. MTU ignore
F. PMTUD
Answer: B F
I did the exam and got this question , there was no option for PMTUD, answer may fall on IP MTU
@ Ciscolad
Are the questions in this premium membership enough to pass the exam?
Can anyone please check question 7?
Question 7 answer is correct:
this is how it looks like on the running configuration on a router when its configured:
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous <<<
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous <<
line vty 0 4
logging synchronous <<
login
=============================================
there is no option to configure logging synchronous under global config:
R2(config)#logging ?
Hostname or A.B.C.D IP address of the logging host
buffered Set buffered logging parameters
buginf Enable buginf logging for debugging
cns-events Set CNS Event logging level
console Set console logging parameters
count Count every log message and timestamp last occurrence
exception Limit size of exception flush output
facility Facility parameter for syslog messages
filter Specify logging filter
history Configure syslog history table
host Set syslog server IP address and parameters
monitor Set terminal line (monitor) logging parameters
on Enable logging to all enabled destinations
origin-id Add origin ID to syslog messages
rate-limit Set messages per second limit
reload Set reload logging level
server-arp Enable sending ARP requests for syslog servers when
first configured
source-interface Specify interface for source address in logging
transactions
trap Set syslog server logging level
userinfo Enable logging of user info on privileged mode enabling
Question 7 answer is correct:
this is how it looks like on the running configuration on a router when its configured:
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous <<<
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous <<
line vty 0 4
logging synchronous <<
login
=============================================
there is no option to configure logging synchronous under global config:
R2(config)#logging ?
Hostname or A.B.C.D IP address of the logging host
buffered Set buffered logging parameters
buginf Enable buginf logging for debugging
cns-events Set CNS Event logging level
console Set console logging parameters
count Count every log message and timestamp last occurrence
exception Limit size of exception flush output
facility Facility parameter for syslog messages
filter Specify logging filter
history Configure syslog history table
host Set syslog server IP address and parameters
monitor Set terminal line (monitor) logging parameters
on Enable logging to all enabled destinations
origin-id Add origin ID to syslog messages
rate-limit Set messages per second limit
reload Set reload logging level
server-arp Enable sending ARP requests for syslog servers when
first configured
source-interface Specify interface for source address in logging
transactions
trap Set syslog server logging level
userinfo Enable logging of user info on privileged mode enabling
Question 7:
Since the question is asking to minimize the possibility of typing commands incorrectly, I think its more basic than people are thinking. When typing in the command-line, we want to make sure that we don’t make mistakes that cause us to retype or correct ourselves.
We understand that “C. Configure the logging synchronous command under the vty” is correct. It can be confirmed directly on router. This configuration will keep your most recent configuration on the prompt constantly showing even when terminal monitoring displays events.
When typing commands in command-line, we can use TAB to auto-fill the command so we don’t have to mistype the words. Therefore “D” would be correct. I think its that simple. Let me know if I’m missing anything.
please share question #10.
Can anyone check Question 10?
it says the answer is There is instability in the network due to route flapping but the explanation is misconfiguration
@NET-Student: Q.10 answers are correct. “Route flapping” in the explanation mentions about answer C.
Question 10 answer
E. The tunnel destination is being routed out of the tunnel interface
is not correct in my opinion. Tunnel destination has to be routed out of tunnel interface to avoid recursive routing.
Aren’t correct answers:
A. Incorrect destination IP addresses are configured on the tunnel – in case configured address is routed inside tunnel
C. There is instability in the network due to route flapping – in case we loose valid routing entry due to flapping
Question 4
What does Call Admission Control require the client to send in order to reserve the bandwidth?
A. SIP flow information
B. Wi-Fi multimedia
C. traffic specification
D. VoIP media session awareness
This question is not covered in 350-401 exam topics. (https://learningcontent.cisco.com/documents/exam-topics/350-401-ENCORE+Blueprint+-+Public.pdf)
Was it appeared in exam before?
Dears
i can’t see the question , is something wrong with my browser or i have to pay ?