Unicast Reverse Path Forwarding
Question 1
Explanation
The Unicast Reverse Path Forwarding feature (Unicast RPF) helps the network guard against malformed or “spoofed” IP packets passing through a router. A spoofed IP address is one that is manipulated to have a forged IP source address. Unicast RPF enables the administrator to drop packets that lack a verifiable source IP address at the router.
Unicast RPF is enabled on a router interface. When this feature is enabled, the router checks packets that arrive inbound on the interface to see whether the source address matches the receiving interface. Cisco Express Forwarding (CEF) is required on the router because the Forwarding Information Base (FIB) is the mechanism checked for the interface match.
Unicast RPF works in one of three different modes:
+ Strict mode: router will perform two checks for all incoming packets on a certain interface. First check is if the router has a matching entry for the source in the routing table. Second check is if the router uses the same interface to reach this source as where it received this packet on.
+ Loose mode: only check if the router has a matching entry for the source in the routing table
+ VRF mode: leverage either loose or strict mode in a given VRF and will evaluate an incoming packet’s source IP address against the VRF table configured for an eBGP neighbor.
Reference: CCIE Routing and Switching v4.0 Quick Reference, 2nd Edition
Question 2
Explanation
When Unicast Reverse Path Forwarding is enabled, the router checks packets that arrive inbound on the interface to see whether the source address matches the receiving interface.
Question 3
Explanation
First we need to understand the “allow-default” keyword here:
Normally, uRPF will not allow traffic that only matches the default route. The “allow-default” keyword will override this behavior and uRPF will allow traffic matched the default route to pass through.
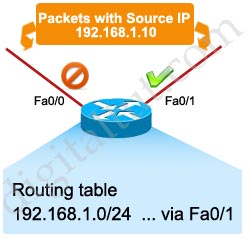
In answer A, The “ip verify unicast source reachable-via rx allow-default” command under interface Fa0/0 enables uRPF strict mode on Fa0/0. Therefore traffic from the 172.16.1.0/24 network (and any traffic) can go through this interface except the 10.0.0.0/8 network because this network is matched on Fa0/1 interface only. The network 10.0.0.0/8 can only enter TUT router from Fa0/1, thus “limiting spoofed 10.0.0.0/8 hosts that could enter router”.
Question 4
Explanation
Unicast Reverse Path Forwarding (uRPF) examines the source IP address of incoming packets. If it matches with the interface used to reach this source IP then the packets are allowed to enter (strict mode).
The syntax of configuring uRPF in interface mode is:
| ip verify unicast source reachable-via {rx | any} [allow-default] [allow-self-ping] [access-list-number] |
| Router(config)#access-list 110 permit ip 192.168.1.0 0.0.0.255 any Router(config)#interface fa0/1 Router(config-if)#ip verify unicast source reachable-via any 110 |
Question 5
Explanation
Unicast Reverse Path Forwarding (uRPF) examines the source IP address of incoming packets. If it matches with the interface used to reach this source IP then the packets are allowed to enter (strict mode).

Unicast RPF is enabled on a router interface. When this feature is enabled, the router checks packets that arrive inbound on the interface to see whether the source address matches the receiving interface. Cisco Express Forwarding (CEF) is required on the router because the Forwarding Information Base (FIB) is the mechanism checked for the interface match.
Unicast RPF works in one of three different modes:
+ Strict mode: router will perform two checks for all incoming packets on a certain interface. First check is if the router has a matching entry for the source in the routing table. Second check is if the router uses the same interface to reach this source as where it received this packet on.
+ Loose mode: only check if the router has a matching entry for the source in the routing table
+ VRF mode: leverage either loose or strict mode in a given VRF and will evaluate an incoming packet’s source IP address against the VRF table configured for an eBGP neighbor.
Reference: CCIE Routing and Switching v4.0 Quick Reference, 2nd Edition
This question only mentioned about “the network to which the packet’s source IP address belongs is found in the router’s FIB” so surely loose mode will accept this packet.
Question 6
Explanation
When a packet is received at the interface where Unicast RPF and ACLs have been configured, the following actions occur:
Step 1: Input ACLs configured on the inbound interface are checked.
Step 2: Unicast RPF checks to see if the packet has arrived on the best return path to the source, which it does by doing a reverse lookup in the FIB table.
Step 3: CEF table (FIB) lookup is carried out for packet forwarding.
Step 4: Output ACLs are checked on the outbound interface.
Step 5: The packet is forwarded.
Reference: http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfrpf.html
Question 7
Question 8
Explanation
The command “ip verify unicast source reachable-via any” enables uRFP in loose mode, which only checks if the router has a matching entry for the source in the routing table.
Question 9
Question 10



Here are the latest dumps:
https://drive.google.com/drive/folders/0B21TuNHP-x2dc2U5MUlNOXFkd2c?usp=drive_web&ddrp=1
What’s uRPF checking first when the packet enters the interface? or when unicast reverse path forwarding is configured on an interface.The answer should be, it is checking for a route in the table for the source.
What if both ACL and a URPF command are present on the interface, then what would it go by first, would it drop the packet if a deny ACL is matched even if the URPF check is successfull? Is this even possible? I just ran test commands on a router, the router accepted both ingress ACL (access-group) as well as the URPF command. Any body can help ?
@Messi
I have been looking into this also and this I the best info I have found.
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfrpf.html
When a packet is received at the interface where Unicast RPF and ACLs have been configured, the following actions occur:
Step 1 Input ACLs configured on the inbound interface are checked.
Step 2 Unicast RPF checks to see if the packet has arrived on the best return path to the source, which it does by doing a reverse lookup in the FIB table.
Step 3 CEF table (FIB) lookup is carried out for packet forwarding.
Step 4 Output ACLs are checked on the outbound interface.
Step 5 The packet is forwarded.
Access Control Lists and Logging
If an ACL is specified in the command, then when (and only when) a packet fails the Unicast RPF check, the ACL is checked to see if the packet should be dropped (using a deny statement in the ACL) or forwarded (using a permit statement in the ACL). Whether a packet is dropped or forwarded, the packet is counted in the global IP traffic statistics for Unicast RPF drops and in the interface statistics for Unicast RPF.
If no ACL is specified in the Unicast RPF command, the router drops the forged or malformed packet immediately and no ACL logging occurs. The router and interface Unicast RPF counters are updated.
Unicast RPF events can be logged by specifying the logging option for the ACL entries used by the Unicast RPF command. Using the log information, administrators can see what source addresses are being used in the attack, the time the packets arrived at the interface, and so on.
What is not supported by Unicast Reverse Path Forwarding interface?
Right Answer: Searchable both.
Expl.: the answer ‘searchable both’, maybe, is trying to say ‘rx’ and ‘any’ that are the two possible ways uRPF works (strict and loose). You can only choose one! The other answers are supported (ping-to self , default-route, ACL).
Let’s see the command:
interface FastEthernet 0/0
ip verify unicast source reachable-via {rx | any} [allow-default] [allow-self-ping] [list]
*the only thing you MUST choose just one is {rx OR any}!
completing my previous post… dump is saying ACL because just router 12000 cannot use that! it’s completely insane that Cisco will get to this specifics in all questions, this way it would be impossible to pass. Dump tries to find googling the easy way to find for an answer.
I have the latest dump for 300-101 route – email me at iastate80 at yahoo dot com.
Who has a latest dumps ??
I feel lost in all the dumps. What is the dump that is really valid ?? Or can find 355Q dump. Help me
I feel lost in all the dumps. What is the dump that is really valid ?? Or can find 355Q dump. Help me
Q6 and Q10-
Same questions with differing answers??
Hello guys, for latest valid dump with continuous update, please contact me at steffyshirls @ gmail .com
Question 6 and 10 contradict each other.
Cisco link confirms ACLs are checked first
Hi friends, I have the valid dump with me and I’m wiling to share. Please contact me via durshen81 @ gmail .com
Passed, if you go the exam study the 21q dumps.
You can find the it-libraries dumps here https://drive.google.com/open?id=0B5mAFqgydmCzNno3dnFocF9HckU
Q6. Correct answer should be C.
Read the question thoroughly: it’s asking what uRPF will check first.
When a packet enters an interface, it will be tested against an inbound acl first, but that is NOT handeld by uRPF
why people trust only with the dumps ? dumps is just for revision. Please refer books and lab videos. If everyone completes CCNP then no point of conducting the exam.
https://www.digitaltut.com/final_flash/Unicast_Reverse_Path_Forwarding/quiz.html
Please advise if Q3 answer is correct for A? or D?
Hi friends, I’m willing to share valid dumps that guarantee you pass. Please contact me via durshen81 @ gmail .com
Question 6
What’s uRPF checking first when the packet enters the interface?
A. It checks the ingress access list
B. It checks the egress access list
C. Route available in FIB or it verifies a reverse patch via the FIB to the source
D. It verifies that the source has a valid CEF adjacency
it says right answer is A, but what if there is no ingress access list??? and by default there is not. then Option C is correct, i guess.
I believe the correct answer for question 6 is C.
The question does not specified that the packet is received on an interface that has an Access-list. If that was the case, then answer would be A.
From How Unicast RPF works section of the below link:
https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfrpf.html#wp1000928
“Unicast RPF checks to see if any packet received at a router interface arrives on the best return path (return route) to the source of the packet. Unicast RPF does this by doing a reverse lookup in the CEF table”
AND…
When a packet is received at the interface where Unicast RPF and ACLs have been configured, the following actions occur:
Step 1 Input ACLs configured on the inbound interface are checked.
Step 2 Unicast RPF checks to see if the packet has arrived on the best return path to the source, which it does by doing a reverse lookup in the FIB table.
Step 3 CEF table (FIB) lookup is carried out for packet forwarding.
Step 4 Output ACLs are checked on the outbound interface.
Step 5 The packet is forwarded.
For Q10
No explaination. Why answer is A ?
I think …….B is correct. If CEF is not enabled uRPF fails as it uses FIB tables to verify source.
Q10
uRPF doesn’t fail it is just having issues :)
CEF is enabled and uRPF is working but asymmetric routing is making problems
this is typical cisco question!
Scored 9xx, used dumps from IT-Libraries. You can find them on the net for free or in the comments here.
Anyone have up-to-date PL Dumps? I’d like to compare to the 477Q and check for differences if possible please send to kokibu67 @ gmail . com
@Digital Q7 answer in the (quiz) is (ALL) but her its (any).
Could you please correct the quiz asap so people don’t get confused.
CORRECT: C. interface GigabitEthernet0/0
ip verify unicast source reachable-via any
The access list check it is refering to is not an interface access list, it is the access list applied to the rpf check command. uRPF allows an acceess list override filter to specify addresses that will be forwarded without checking the uRPF validity.
If an ACL is specified in the command, then when (and only when) a packet fails the Unicast RPF check, the ACL is checked to see if the packet should be dropped (using a deny statement in the ACL) or forwarded (using a permit statement in the ACL). Whether a packet is dropped or forwarded, the packet is counted in the global IP traffic statistics for Unicast RPF drops and in the interface statistics for Unicast RPF.
About Question 6, right answer is A:
Step 1 Input ACLs configured on the inbound interface are checked.
Step 2 Unicast RPF checks to see if the packet has arrived on the best return path to the source, which it does by doing a reverse lookup in the FIB table.
Step 3 CEF table (FIB) lookup is carried out for packet forwarding.
Step 4 Output ACLs are checked on the outbound interface.
Step 5 The packet is forwarded.
You can read this:
https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfrpf.html
New urpf question on exam, I can’t remember whole question sorry but it’s something along the lines of
“What is valid options for configuring uRPF”
1) Enabled globally
2) Enabled on interface
3) both strict and loose can use the keyword any
4) strict mode may drop legitimate traffic
5) Can’t remember last option
Just noticed the question i posted above is on New ROUTE Questions – Part 4 question 5 :)
Question 10 explantion:
Unicast RPF configured in strict mode may drop legitimate traffic that is received on an interface that was not the router’s choice for sending return traffic. Dropping this legitimate traffic could occur when asymmetric routing paths are present in the network.
Care must be taken to ensure that the appropriate Unicast RPF mode (loose or strict) is configured during the deployment of this feature because it can drop legitimate traffic. Although asymmetric traffic flows may be of concern when deploying this feature, Unicast RPF loose mode is a scalable option for networks that contain asymmetric routing paths.
from: https://www.cisco.com/c/en/us/about/security-center/unicast-reverse-path-forwarding.html
I have seen Q6 shown with both answers A and C being correct. I was a bit lost so I did my own research and found the following information:
A: It checks the ingress ACL
C: If checks the FIB and verifies a reverse path via the FIB to the source
Several people above have posted stale links to documentation that no longer work (error 404). Here is a current link that explains the urpf process:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_data_urpf/configuration/xe-3s/sec-data-urpf-xe-3s-book/urpf-acl-sup.html
As per the above article:
Before forwarding a packet that is received at the interface on which Unicast RPF and ACLs have been configured, Unicast RPF does the following checks:
1) If input ACLs are configured on the inbound interface.
2) If the packet has arrived on the best return path to the source by doing a reverse lookup in the FIB table.
3) Does a lookup of the Cisco Express Forwarding table for packet forwarding.
4) Checks output ACLs on the outbound interface.
5) Forwards the packet.
The problem is the question doesn’t specify if there is an ACL on the interface or not. However, if you think about the logic behind the question, they are simply asking what the first step is IN GENERAL. I believe if the answer were intended to be C, the question would specify the presence of an ACL on the interface.